Risk Management
IT Dept. serves as the unit responsible for the Company’s information security. One IT officer and several IT engineers are delegated to set forth the Company’s information security policy, plan the information security measures, execute related information security operations, and review, amend, and supplement the operations periodically each year to ensure the Group’s information security. In consideration of the importance of information security, the responsible unit shall report the Company’s information security practices and implementation thereof to the Board of Directors periodically each year.
-
Purpose:
- The Company sets the information security policy targets in order to ensure the availability, integrity and confidentiality of the information.
-
Target:
-
(1) Availability:
Ensure that various information assets can provide real-time and correct services to satisfy the users’ demand. -
(2) Integrity:
Classify the information assets subject to the importance thereof, and provide adequate protection to ensure the integrity of information assets. -
(3) Confidentiality:
Grade the confidentiality of information adequately and provide adequate regulations and protection subject to the confidentiality level.
-
Scope:
- Enactment of and evaluation of the information security policy
- Information security duties and division of labor within the organization
- HR security and training
- Information asset management
- Access control and password management
- Password management
- Physical and environmental security
- Operations security management
- Network security management
- Access to and development and maintenance of IT system
- Vendor security management
- IT security incident management
- Business continuity management
- Compliance (legality)
The information security-related measures are stated as follows:
| Scope | Specific management method |
|---|---|
| Firewall protection | Firewall setting access rules |
| User’s online behavior control mechanism | Control user’s online behavior via the automatic website protection system. |
| Anti-virus software policy | Use multiple anti-virus software packages, update the virus code automatically, and execute full scanning once a week, in order to reduce the chance of getting infected. |
| Operating system update | The operating system shall update automatically. Otherwise, the IT Dept. shall help update the system. |
| Mail security control | The automatic mail threat scanning system is in place. Before the user’s receipt of any mails, it is necessary to prevent unsafe attachments, phishing mails and spam, and expand the scope of protection against malicious links. |
| Website protection mechanism | The website is equipped with a firewall to block cyber attacks from outside. |
| Data backup mechanism | The important IT system database shall set the backup on a daily basis and also per hour. |
| Remote storage | The backup files in the server and IT system shall be stored at branch companies separately. |
| Uploading of important files to the server | Each department’s important files shall be uploaded to the server for storage. IT Dept. shall maintain the backup files collectively. |
| Data center inspection record form | The information center inspection record form records the temperature and humidity, updates the anti-virus software and network traffic of the control room. |
| IT system, access to software and access control | The users who wish to install any system or software shall file an application therefor. Upon the unit supervisor’s approval, IT Dept. will authorize the installation upon confirmation. The application for additional procurement, if any, shall be filed by the unit. After that, IT Dept. would help with the installation for physical control. |
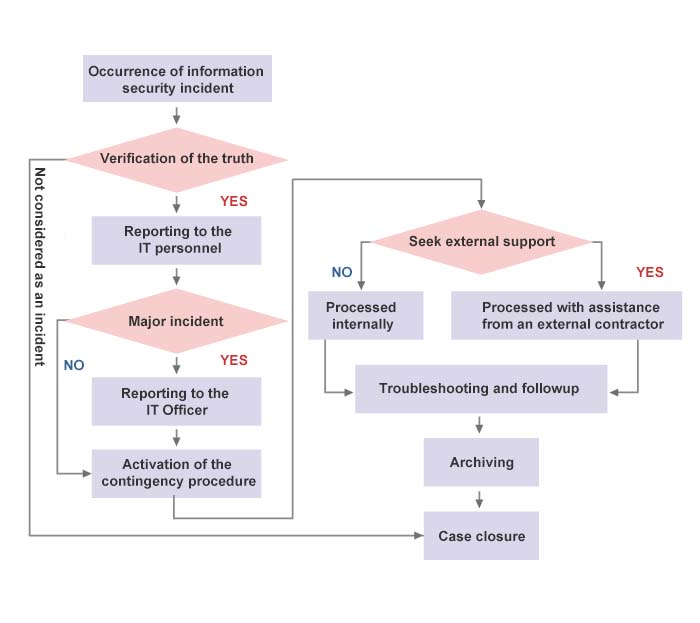
The Company’s information security incident reporting procedure is stated as follows. Any information security incident shall be reported and processed in accordance with said procedure.